共计 8420 个字符,预计需要花费 22 分钟才能阅读完成。
CA 服务器:192.168.75.131
httpd 服务器:192.168.75.128
操作系统版本:RedHat 6.5(x_86_64)
一、安装 openssl
1、源码安装:
openssl:wget http://www.openssl.org/source/openssl-1.0.0a.tar.gz
# tar xvf openssl-1.0.0a.tar.gz
# cd openssl-1.0.0a
# ./config –prefix=/usr/local/openssl
# make && make install
2、RPM 安装
yum install openssl openssl-devel -y
二、安装 Apache
1、源码安装 httpd 参考:编译安装 Apache(httpd-2.4.18)
–enable-so #动态模块支持
–enable-ssl #开启 ssl 模块支持
–with-ssl=/usr/local/openssl 使用编译版本的 openssl,如果不指定,则使用 RPM 版本的 openssl
编译参数:
./configure –prefix=/usr/local/apache –enable-so –enable-ssl –enable-cgi –enable-rewrite –with-zlib –with-pcre=/usr/local/pcre –with-apr=/usr/local/apr –with-apr-util=/usr/local/apr-util –enable-mpms-shared=all –with-mpm=event –enable-proxy –enable-proxy-http –enable-proxy-ajp –enable-proxy-balancer –enable-lbmethod-heartbeat –enable-heartbeat –enable-slotmem-shm –enable-slotmem-plain –enable-watchdog –with-ssl=/usr/local/openssl
2、RPM 包安装 httpd
需要安装 mod_ssl 模块
# yum install httpd mod_ssl -y
三、CA 服务器生成自签证书(在 CA 服务器:192.168.75.131 上操作)
# yum install openssl -y
# cd /etc/pki/CA/
# (umask 077;openssl genrsa -out private/cakey.pem 2048) #生成私钥
# ll private/
total 4
-rw——-. 1 root root 1679 Feb 18 17:49 cakey.pem
生成自签证书的时候会有很多选项需要填写,如果不想填,可以编辑配置文件,更换默认值
# cd ../tls/
# diff openssl.cnf openssl.cnf.orig
130c130
< countryName_default= CN
—
> countryName_default= XX
135c135
< stateOrProvinceName_default= GuangDong
—
> #stateOrProvinceName_default= Default Province
138c138
< localityName_default= ShenZhen
—
> localityName_default= Default City
141c141
< 0.organizationName_default= SmallFish Company Ltd
—
> 0.organizationName_default= Default Company Ltd
148c148
< organizationalUnitName_default= Tech
—
> #organizationalUnitName_default=
# vim ../tls/openssl.cnf # 保证 dir 是在 /etc/pki/CA 目录
[CA_default]
dir = /etc/pki/CA # Where everything is kept
# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3665 #根据私钥给自己生成一个自签证书,这个证书可以给用户使用的
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [CN]:
State or Province Name (full name) [GuangDong]:
Locality Name (eg, city) [ShenZhen]:
Organization Name (eg, company) [SmallFish Company Ltd]: #给别人签发的公司也必须是这个
Organizational Unit Name (eg, section) [Tech]:
Common Name (eg, your name or your server’s hostname) []:ca.smallfish.com #发给自己的证书
Email Address []:admin@smallfish.com
# cd /etc/pki/CA/
# touch index.txt
# echo 00 >serial
# tree .
.
├── cacert.pem
├── certs
├── crl
├── index.txt
├── newcerts
├── private
│ └── cakey.pem
└── serial
四、web 服务器端, 生成证书颁发请求(在 192.168.75.128 上操作)
# cd /usr/local/apache/conf
# mkdir ssl
# cd ssl/
#(umask 077;openssl genrsa 1024 > httpd.key) #生成密钥
Generating RSA private key, 1024 bit long modulus
…….++++++
………………………..++++++
e is 65537 (0x10001)
# ll
total 4
-rw——-. 1 root root 887 Feb 8 18:40 httpd.key
# openssl req -new -key httpd.key -out httpd.csr #生成证书申请请求
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [XX]:CN #信息必须和 CA 端保持一致
State or Province Name (full name) []:GuangDong #信息必须和 CA 端保持一致
Locality Name (eg, city) [Default City]:ShenZhen #信息必须和 CA 端保持一致
Organization Name (eg, company) [Default Company Ltd]:SmallFish Company Ltd # 必须是 CA 证书中填写的是同一个公司,不如后面生成公司证书的时候会报错
Organizational Unit Name (eg, section) []:Tech
Common Name (eg, your name or your server’s hostname) []:www.vip.com
Email Address []:www.vip.com
Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@master ssl]#
# scp httpd.csr 192.168.75.131:/tmp #用 U 盘拷贝,发邮件都可以
五、CA 服务器签发证书(在 CA 服务器:192.168.75.131 上操作)
# openssl ca -in /tmp/httpd.csr -out /tmp/httpd.crt -days 3650 #CA 进行签署证书,公司名称不一样,会报错
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
The organizationName field needed to be the same in the
CA certificate (SmallFish Company Ltd) and the request (vip Ltd)
# openssl ca -in /tmp/httpd.csr -out /tmp/httpd.crt -days 3650 #CA 进行签署证书
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 0 (0x0)
Validity
Not Before: Feb 18 10:10:26 2016 GMT
Not After : Feb 15 10:10:26 2026 GMT
Subject:
countryName = CN
stateOrProvinceName = GuangDong
organizationName = SmallFish Company Ltd
organizationalUnitName = Tech
commonName = www.vip.com
emailAddress = www.vip.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
68:4F:A6:95:E8:65:0D:FE:9E:E2:81:31:8A:AF:69:3A:4C:43:E0:94
X509v3 Authority Key Identifier:
keyid:AA:27:66:F1:0F:7A:7C:CA:CD:85:95:1F:D5:92:5A:36:23:FE:1A:36
Certificate is to be certified until Feb 15 10:10:26 2026 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
# cat index.txt
V260215101026Z00unknown/C=CN/ST=GuangDong/O=SmallFish Company Ltd/OU=Tech/CN=www.vip.com/emailAddress=www.vip.com
# cat serial
01
# tree .
.
├── cacert.pem
├── certs
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── newcerts
│ └── 00.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old
4 directories, 8 files
# scp /tmp/httpd.crt 192.168.75.128:/usr/local/apache/conf/ssl #拷贝证书到 Web 服务器
# rm /tmp/httpd.crt /tmp/httpd.csr #CA 服务器端制作完毕之后可以删除掉 web 服务器端证书
六、web 服务器端配置 openssl(在 192.168.75.128 上操作)
vim /usr/local/apache/conf/extra/httpd-ssl.conf
<VirtualHost _default_:443>
DocumentRoot “/usr/local/apache/htdocs” #和 80 端口文档目录的保持一致,不然和 80 访问的内容不一样
ServerName www.vip.com:443
ServerAdmin admin@vip.com
ErrorLog “/usr/local/apache/logs/error_log”
TransferLog “/usr/local/apache/logs/access_log”
SSLEngine on
SSLCertificateFile “/usr/local/apache/conf/ssl/httpd.crt”
SSLCertificateKeyFile “/usr/local/apache/conf/ssl/httpd.key”
# vim /usr/local/apache/conf/httpd.conf #打开下面的注释
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so
LoadModule ssl_module modules/mod_ssl.so
LoadModule slotmem_shm_module modules/mod_slotmem_shm.so
Include conf/extra/httpd-ssl.conf
# /usr/local/apache/bin/httpd -t
Syntax OK
# httpd -M| grep ssl_mod #查看是否支持 ssl_module
ssl_module (shared)
# /usr/local/apache/bin/apachectl start
# lsof -i:80
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
httpd 13445 root 4u IPv6 349321 0t0 TCP *:http (LISTEN)
httpd 13446 daemon 4u IPv6 349321 0t0 TCP *:http (LISTEN)
httpd 13447 daemon 4u IPv6 349321 0t0 TCP *:http (LISTEN)
httpd 13448 daemon 4u IPv6 349321 0t0 TCP *:http (LISTEN)
# lsof -i:443
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
httpd 13445 root 6u IPv6 349329 0t0 TCP *:https (LISTEN)
httpd 13446 daemon 6u IPv6 349329 0t0 TCP *:https (LISTEN)
httpd 13447 daemon 6u IPv6 349329 0t0 TCP *:https (LISTEN)
httpd 13448 daemon 6u IPv6 349329 0t0 TCP *:https (LISTEN)
七、访问验证
1、在 win hosts 文件中添加
C:\WINDOWS\System32\drivers\etc\hosts
192.168.85.128 www.vip.com
2、安装证书
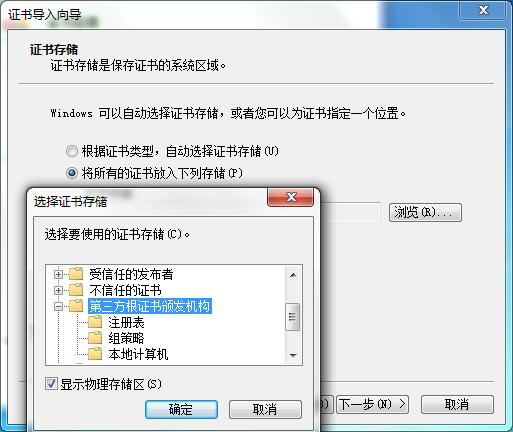
拷贝 CA 服务器中的证书(/etc/pki/CA/cacert.pem)到客户端,重命名为 cacert.crt,双击运行安装,导入到浏览器,用浏览器打开


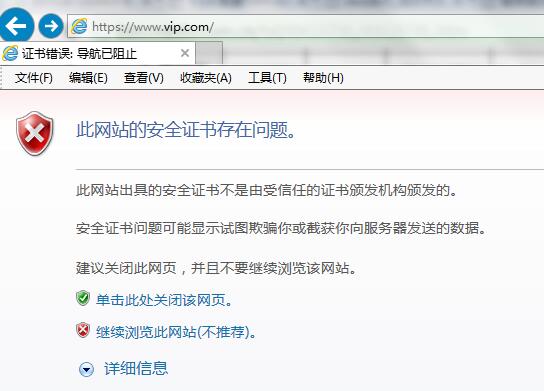
3、访问:
https://www.vip.com/
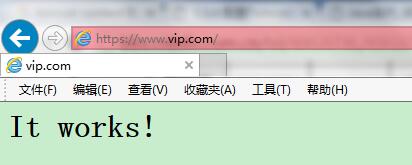
http://www.vip.com/
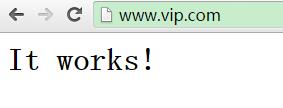
八、遇到的问题
问题 1:
# /usr/local/apache2/bin/apachectl start
AH00526: Syntax error on line 51 of /usr/local/apache2/conf/extra/httpd-ssl.conf:
Invalid command ‘SSLCipherSuite’, perhaps misspelled or defined by a module not included in the server configuration
解决 1:
# vi /usr/local/apache2/conf/httpd.conf
LoadModule ssl_module modules/mod_ssl.so
问题 2:
# /usr/local/apache2/bin/apachectl start
AH00526: Syntax error on line 76 of /usr/local/apache2/conf/extra/httpd-ssl.conf:
SSLSessionCache: ‘shmcb’ session cache not supported (known names:). Maybe you need to load the appropriate socache module (mod_socache_shmcb?).
解决 2:
# vi /usr/local/apache2/conf/httpd.conf
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so
问题 3:
The countryName field needed to be the same in the
CA certificate (cn) and the request (sh)
解决 3:证书的国家名称,省名要相同
九、注意:
SSL 会话不能基于主机名区分,服务器只有一个 ip 地址,只能为一个主机提供 ssl 的功能,如果有很多基于域名的虚拟主机,ssl 只能提供给其中的一个虚拟主机使用.
更多 OpenSSL 相关内容可以查看以下的有用链接:
使用 OpenSSL 命令行构建 CA 及证书 http://www.linuxidc.com/Linux/2015-10/124682.htm
Ubuntu 安装 OpenSSL http://www.linuxidc.com/Linux/2015-10/124001.htm
通过 OpenSSL 提供 FTP+SSL/TLS 认证功能,并实现安全数据传输 http://www.linuxidc.com/Linux/2013-05/84986.htm
Linux 下使用 OpenSSL 生成证书 http://www.linuxidc.com/Linux/2015-05/117034.htm
利用 OpenSSL 签署多域名证书 http://www.linuxidc.com/Linux/2014-10/108222.htm
在 OpenSSL 中添加自定义加密算法 http://www.linuxidc.com/Linux/2015-08/121749.htm
OpenSSL 的详细介绍:请点这里
OpenSSL 的下载地址:请点这里
本文永久更新链接地址:http://www.linuxidc.com/Linux/2016-02/128569.htm













