共计 4467 个字符,预计需要花费 12 分钟才能阅读完成。
利用 gns3 配置了基于 cisco asa 的 ssl 链接测试,cloud- 1 链接本地网络,测试通过
1、配置目标:便于移动办公用户接入公司内部网络,通过内部网络访问 ecs 服务器
2、材料:gns3、asa、anyconnect-win、c7200、pc
3、常规网络结构如下:
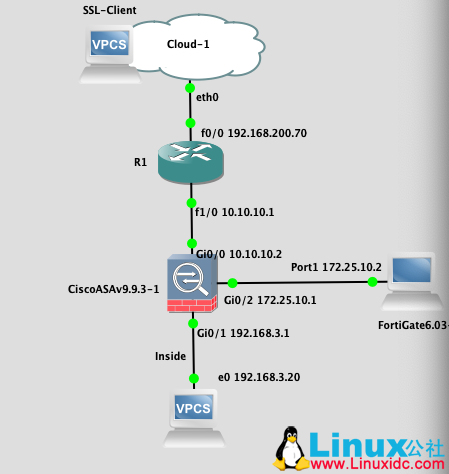
说明:
1、r1 路由器为边界路由器:主要配置为接入互联网和配置防火墙 outside 的地址映射
2、asa 负责 ssl 的请求终结,提供 inside 端的 nat 功能
3、fortGate 不在本次实验范围之内
配置:
主要是 asa 的接入配置:
ASA Version 9.9(2)
!
hostname ciscoasa
enable password $sha512$5000$fXJ5sJ0tyZpekqU23FSJqw==$9adIvXwEh3hZgQjRaYxCwg== pbkdf2
names
ip local pool ssluser 172.17.1.10-172.17.1.20 mask 255.255.255.0
!– 远程用户分配地址 –!
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 10.10.10.2 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.3.1 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
nameif dmz
security-level 60
ip address 172.25.10.1 255.255.255.0
!
…
ftp mode passive
!– 需要开启 –!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network local
subnet 192.168.3.0 255.255.255.0
object network nat-addr
host 10.10.10.5
object network NETWORK_OBJ_192.168.3.0_24
subnet 192.168.3.0 255.255.255.0
object network ssl-addr
range 172.16.1.10 172.16.1.20
description ssl user address
object network NETWORK_OBJ_172.17.1.0_27
subnet 172.17.1.0 255.255.255.224
access-list outside_access_in extended permit icmp any any log debugging
access-list outside_access_in extended permit ip any any log debugging
access-list split-acl standard permit 192.168.3.0 255.255.255.0
access-list split-acl standard permit any4
pager lines 23
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu dmz 1500
no failover
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 8192
nat (inside,outside) source static NETWORK_OBJ_192.168.3.0_24 NETWORK_OBJ_192.168.3.0_24 destination static NETWORK_OBJ_172.17.1.0_27 NETWORK_OBJ_172.17.1.0_27 no-proxy-arp route-lookup
!
object network local
nat (inside,outside) dynamic nat-addr
object network NETWORK_OBJ_172.17.1.0_27
nat (outside,outside) dynamic 10.10.10.6
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 10.10.10.1 1
!– 本地数据库验证
aaa authentication http console LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
http server enable
http 0.0.0.0 0.0.0.0 outside
no snmp-server location
no snmp-server contact
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=192.168.200.55,CN=ciscoasa
keypair ASDM_LAUNCHER
crl configure
crypto ca trustpool policy
auto-import
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
certificate 2bd75b5c
……
44783f1c a8d4cb06 5222721c 2fee837e 31bf194e 15e1c0fd
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside client-services port 443
crypto ikev2 remote-access trustpoint ASDM_Launcher_Access_TrustPoint_0
telnet timeout 5
ssh stricthostkeycheck
ssh 0.0.0.0 0.0.0.0 outside
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl trust-point ASDM_Launcher_Access_TrustPoint_0
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 outside
web***
enable outside
anyconnect image disk0:/anyconnect-win-4.6.00362-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-dart-win-2.5.3046-k9.pkg 2
anyconnect profiles cccrop_client_profile disk0:/cccrop_client_profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy DfltGrpPolicy attributes
***-tunnel-protocol ikev1 l2tp-ipsec ssl-clientless
group-policy GroupPolicy_cccrop internal
!– 在此可以 split 路由 –
!– 本测试没有配置 list
group-policy GroupPolicy_cccrop attributes
wins-server none
dns-server value x.x.x.x
***-tunnel-protocol ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list none
default-domain none
web***
anyconnect profiles value cccrop_client_profile type user
dynamic-access-policy-record DfltAccessPolicy
username user1 password $shGmZ5Er3G2XtZWUbjqf4g==$fJtspAnifM4BGWpl7xA== pbkdf2
tunnel-group cccrop type remote-access
tunnel-group cccrop general-attributes
address-pool ssluser
default-group-policy GroupPolicy_cccrop
tunnel-group cccrop web***-attributes
group-alias cccrop enable
!
……
!
service-policy global_policy global
Cryptochecksum:e8a82b90a84e0f3125f6ae12ffc3d1fc
: end
:
















