共计 4547 个字符,预计需要花费 12 分钟才能阅读完成。
OpenSSL 简介
OpenSSL 是一种加密工具套件,可实现安全套接字层(SSL v2 / v3)和传输层安全性(TLS v1)网络协议以及它们所需的相关加密标准。
openssl 命令行工具用于从 shell 程序使用 OpenSSL 加密库的各种加密功能。它可以用于:
- 创建和管理私钥,公钥和参数
- 公钥加密操作
- 创建 X.509 证书,CSR 和 CRL
- 消息摘要的计算
- 使用密码进行加密和解密
- SSL / TLS 客户端和服务器测试
- 处理 S / MIME 签名或加密的邮件
- 时间戳记请求,生成和验证
openssl 配置文件及三种策略
| 配置文件 | |
| /etc/pki/tls/openssl.cnf | |
| 三种策略 | |
| match(匹配):要求申请填写的信息跟 CA 设置信息必须一致 | |
| optional(可选):可有可无,跟 CA 设置信息可不一致 | |
| supplied(提供):必须填写这项申请信息 |
创建私有 CA 和申请、颁发证书文件(以下操作都是在一台机器上执行)
1. 创建所需要的文件
| [] | |
| [] | |
| [] |
2.CA 自签证书
2.1 生成私钥
| [] | |
| Generating RSA private key, 2048 bit long modulus | |
| ...................................................................................+++ | |
| .+++ | |
| e is 65537 (0x10001) |
2.2 生成自签名证书
| [root@CentOS7 CA]# openssl req -new -x509 -key private/cakey.pem -days 3650 -out cacert.pem | |
| You are about to be asked to enter information that will be incorporated | |
| into your certificate request. | |
| What you are about to enter is what is called a Distinguished Name or a DN. | |
| There are quite a few fields but you can leave some blank | |
| For some fields there will be a default value, | |
| If you enter '.', the field will be left blank. | |
| ----- | |
| Country Name (2 letter code) [XX]:CN | |
| State or Province Name (full name) []:beijing | |
| Locality Name (eg, city) [Default City]:beijing | |
| Organization Name (eg, company) [Default Company Ltd]:abc | |
| Organizational Unit Name (eg, section) []:IT | |
| Common Name (eg, your name or your server's hostname) []:hechunping | |
| Email Address []:root@abc.com | |
| 选项说明:-new:生成新证书签署请求 | |
| -x509:专用于 CA 生成自签证书 | |
| -key:生成请求时用到的私钥文件 | |
| -days n:证书的有效期限 | |
| -out /PATH/TO/SOMECERTFILE: 证书的保存路径 |
3. 颁发证书
3.1 在需要使用证书的主机生成证书请求(本实验是在本机)
3.1.1 生成私钥
| [] | |
| Generating RSA private key, 2048 bit long modulus | |
| ..................................................+++ | |
| ...............................+++ | |
| e is 65537 (0x10001) |
3.1.2 生成证书申请文件
| [root@CentOS7 CA]# openssl req -new -key /data/test.key -out /data/test.csr | |
| You are about to be asked to enter information that will be incorporated | |
| into your certificate request. | |
| What you are about to enter is what is called a Distinguished Name or a DN. | |
| There are quite a few fields but you can leave some blank | |
| For some fields there will be a default value, | |
| If you enter '.', the field will be left blank. | |
| ----- | |
| Country Name (2 letter code) [XX]:CN | |
| State or Province Name (full name) []:beijing | |
| Locality Name (eg, city) [Default City]:beijing | |
| Organization Name (eg, company) [Default Company Ltd]:abc | |
| Organizational Unit Name (eg, section) []:IT | |
| Common Name (eg, your name or your server's hostname) []:hechunping | |
| Email Address []:root@abc.com | |
| Please enter the following 'extra' attributes | |
| to be sent with your certificate request | |
| A challenge password []: | |
| An optional company name []: |
3.2 将证书申请文件传输给 CA(两台不同的主机可以使用 scp 命令传输)
3.3CA 签署证书,并将证书颁发给请求者
| [root@CentOS7 CA]# openssl ca -in /data/test.csr -out certs/test.crt -days 100 | |
| Using configuration from /etc/pki/tls/openssl.cnf | |
| Check that the request matches the signature | |
| Signature ok | |
| Certificate Details: | |
| Serial Number: 1 (0x1) | |
| Validity | |
| Not Before: Nov 10 13:45:34 2019 GMT | |
| Not After : Feb 18 13:45:34 2020 GMT | |
| Subject: | |
| countryName = CN | |
| stateOrProvinceName = beijing | |
| organizationName = abc | |
| organizationalUnitName = IT | |
| commonName = hechunping | |
| emailAddress = root@abc.com | |
| X509v3 extensions: | |
| X509v3 Basic Constraints: | |
| CA:FALSE | |
| Netscape Comment: | |
| OpenSSL Generated Certificate | |
| X509v3 Subject Key Identifier: | |
| 4C:AE:F0:13:F0:CD:8F:B5:F7:3F:1B:C8:E4:77:91:02:9E:88:6B:5A | |
| X509v3 Authority Key Identifier: | |
| keyid:E3:C1:5E:6D:94:5E:F2:AE:16:67:79:2C:69:B5:B9:10:D9:E0:51:BE | |
| Certificate is to be certified until Feb 18 13:45:34 2020 GMT (100 days) | |
| Sign the certificate? [y/n]:y | |
| 1 out of 1 certificate requests certified, commit? [y/n]y | |
| Write out database with 1 new entries | |
| Data Base Updated | |
| 注意:默认要求 countryName(国家),stateOrProvinceName(省),organizationName(公司)三项必须和 CA 一致 |
3.4 查看证书中的信息
[root@CentOS7 CA]# openssl x509 -in certs/test.crt -noout -text|issuer|subject|serial|dates
3.5 查看指定编号的证书状态
| [] | |
| Using configuration from /etc/pki/tls/openssl.cnf | |
| 01=Valid (V) |
4. 吊销证书
4.1 在客户端获取要吊销的证书的 serial
| [root@CentOS7 CA]# openssl x509 -in certs/test.crt -noout -serial -subject | |
| serial=01 | |
| subject= /C=CN/ST=beijing/O=abc/OU=IT/CN=hechunping/emailAddress=root@abc.com |
4.2 在 CA 上,根据客户提交的 serial 与 subject 信息,对比检验是否与 index.txt 文件中的信息一致
| [root@CentOS7 CA]# cat index.txt | |
| V 200218134534Z 01 unknown /C=CN/ST=beijing/O=abc/OU=IT/CN=hechunping/emailAddress=root@abc.com |
4.2.1 吊销证书
| [root@CentOS7 CA]# openssl ca -revoke newcerts/01.pem | |
| Using configuration from /etc/pki/tls/openssl.cnf | |
| Revoking Certificate 01. | |
| Data Base Updated |
4.2 指定第一个吊销证书的编号,注意:第一次更新证书吊销列表前才需要执行。
[root@CentOS7 CA]# echo 01 > crlnumber
4.3 更新证书吊销列表
| [root@CentOS7 CA]# openssl ca -gencrl -out crl.pem | |
| Using configuration from /etc/pki/tls/openssl.cnf |
4.4 查看 crl 文件
[root@CentOS7 CA]# openssl crl -in crl.pem -noout -text
将申请下来的证书导出到 windows 中查看
1. 在 windows 上按 ”win+R” 键,然后运行 ”certmgr.msc” 命令。
2. 找到“受信任的根证书颁发机构”右键单击“所有任务”—>“导入”,然后按照向导选择在 Linux 申请下来的证书。
3. 查看证书信息 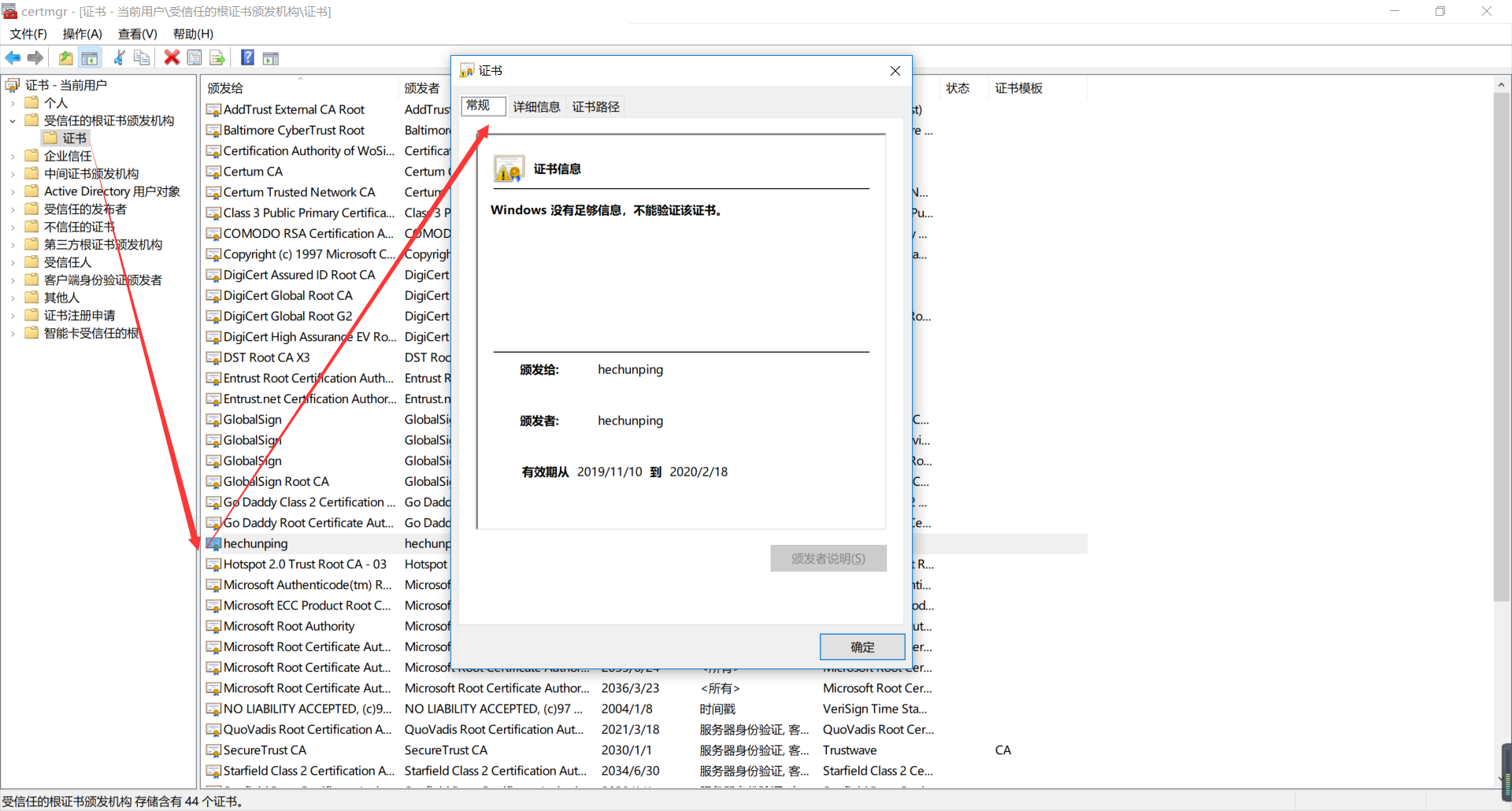
正文完
星哥玩云-微信公众号
















